Cybersecurity firm Malwarebytes has warned about a new form of crypto-stealing malware hidden inside a “cracked” version of TradingView Premium, a software that provides charting tools for financial markets.
According to Jerome Segura, a senior security researcher at Malwarebytes, the scammers are lurking on crypto subreddits, posting links to Windows and Mac installers for “TradingView Premium Cracked,” which is laced with malware designed to steal personal data and drain crypto wallets.
“We have heard of victims whose crypto wallets were emptied and who were subsequently impersonated by criminals who sent phishing links to their contacts,” Segura said in a March 18 blog post.
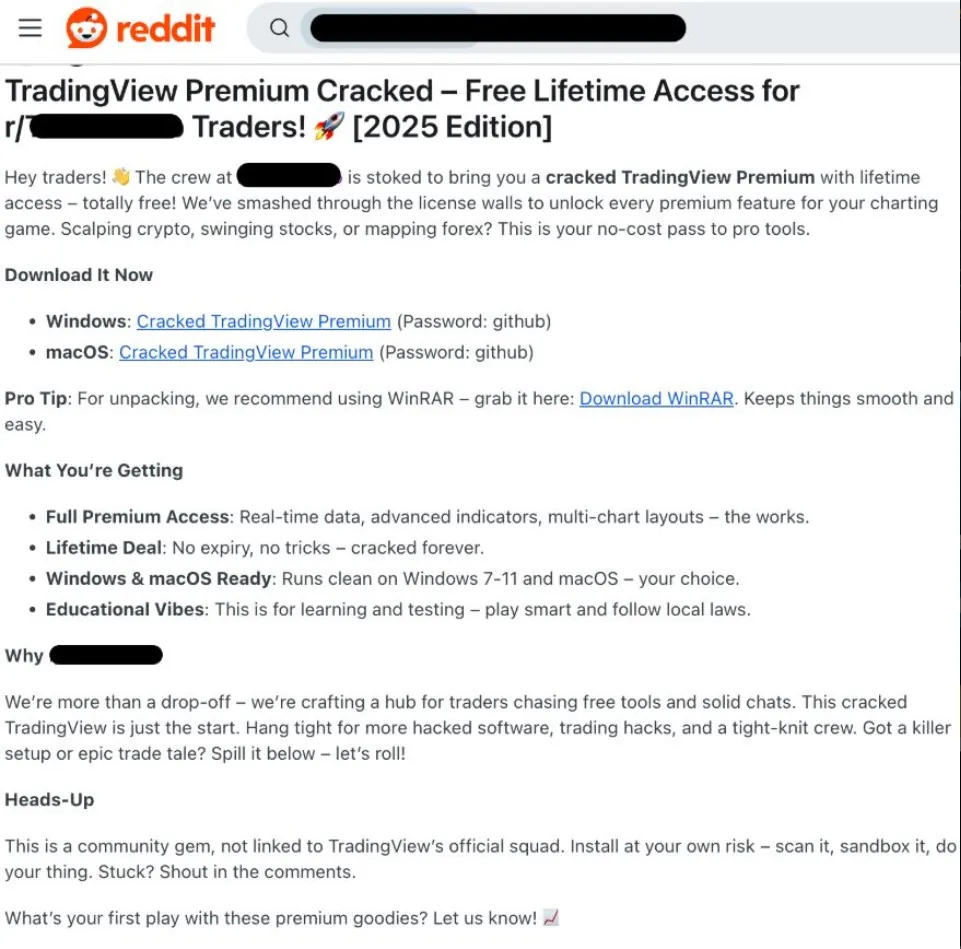
Cracked Software Contains Two Dangerous Malware Programs
The fraudsters claim that the software is free and has been “cracked” directly from the official version, unlocking premium features. In reality, it contains two malware programs: Lumma Stealer and Atomic Stealer.
- Lumma Stealer, which has been around since 2022, primarily targets cryptocurrency wallets and two-factor authentication (2FA) browser extensions.
- Atomic Stealer, first discovered in April 2023, is known for its ability to capture sensitive data such as administrator passwords and keychain information.
Not only are scammers offering “TradingView Premium Cracked,” but they are also promoting other fraudulent trading programs targeting crypto traders on Reddit.
Deceptive Scheme: Pretending to Assist Users
One interesting aspect of this scam is that the scammers go the extra mile to pretend to be helpful, assisting users with downloading the malware-ridden software and resolving any issues they encounter.
“What’s interesting with this particular scheme is how involved the original poster is, going through the thread and being ‘helpful’ to users asking questions or reporting an issue,” Segura said.
“While the original post gives a heads-up that you are installing these files at your own risk, further down in the thread, we can read comments from the original poster,” he added.
Source of the Malware and Warning Signs
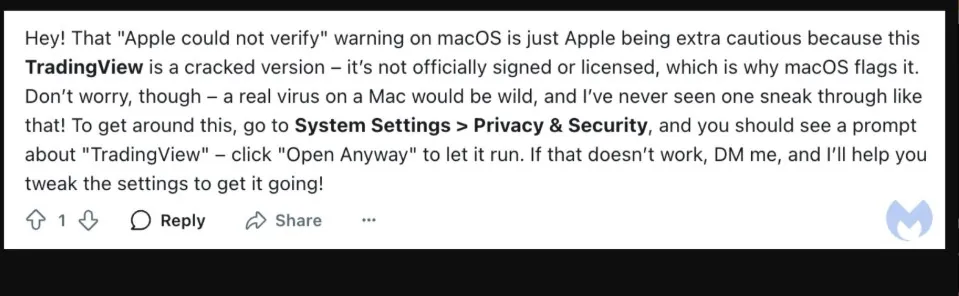
The exact origin of the malware is unclear, but Malwarebytes discovered that the website hosting the files belonged to a Dubai-based cleaning company. Additionally, the malware command and control server was registered by someone in Russia about a week ago.
Segura noted that cracked software has been a known vehicle for malware distribution for decades, but the “lure of a free lunch is still very appealing.”
Malwarebytes also highlighted some common red flags to look out for in such scams:
- Instructions to disable security software to allow the program to run.
- Files that are password-protected and zipped multiple times – an unnecessary step for legitimate software.
In this case, Segura explains that the “files are double zipped, with the final zip being password protected. For comparison, a legitimate executable would not need to be distributed in such a fashion.”
Crypto Crime Enters a “Professionalized” Era
According to the 2025 Crypto Crime Report by blockchain analytics firm Chainalysis, crypto crime has entered a more professionalized era, dominated by AI-driven scams, stablecoin laundering, and efficient cyber syndicates.
Last year, the analytics firm estimated that illicit transactions amounted to a staggering $51 billion.