According to blockchain security firm Cyvers, the attack occurred on February 12, with the stolen funds being transferred to Ethereum and funneled through Railgun for laundering. However, due to Railgun’s protocol policies, the assets were ultimately returned to the original address.
“zkLend has suffered a $4.9 million exploit on the Starknet network. The stolen funds were bridged to Ethereum and laundered via Railgun, but due to protocol policies, Railgun returned the funds to the original address,” Cyvers reported.
In response, zkLend has extended an offer to the attacker, proposing a 10% bounty in exchange for the return of the remaining funds and immunity from legal action.
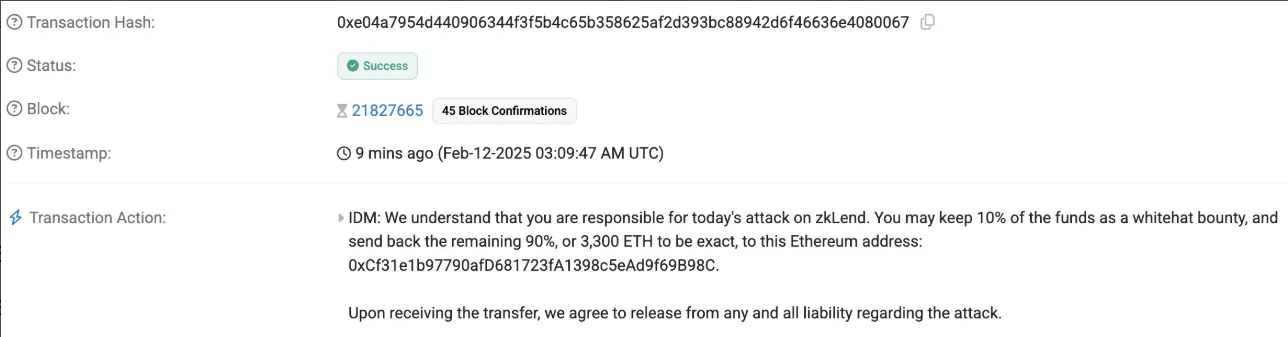
“We understand that you are responsible for today’s attack on zkLend. You may keep 10% of the funds as a whitehat bounty and return the remaining 90%—exactly 3,300 ETH,” the protocol stated.
The firm also issued a firm deadline: “We are working closely with security firms and law enforcement. If we do not hear from you by 00:00 UTC on February 14, 2025, we will move forward with the necessary steps to track and prosecute you.”
While crypto-related hacks saw a 44% year-over-year decline in January 2025, cybercriminals still managed to steal over $73 million that month. Experts warn that the threat remains significant, as 2024 saw hackers siphon $2.3 billion across 165 incidents—representing a 40% increase from 2023’s $1.69 billion in stolen assets.